Best Services
Advanced smartphone protection against viruses, spyware and thieves






Connect boldly to public Wi-Fi with our bank-grade, 256-bit AES encryption. We keep all your online activity private and away from hackers, nosy neighbors and curious agencies. And it doesn’t hurt that you can access your favorite content worldwide.

Advanced smartphone protection against viruses, spyware and thieves
Premium protection and privacy for your small business

Give your small and medium business the security it needs. From antivirus and spyware protection to data transaction and file server security, our Business Edition products have all the features your business needs to survive and thrive beyond cyber threats.



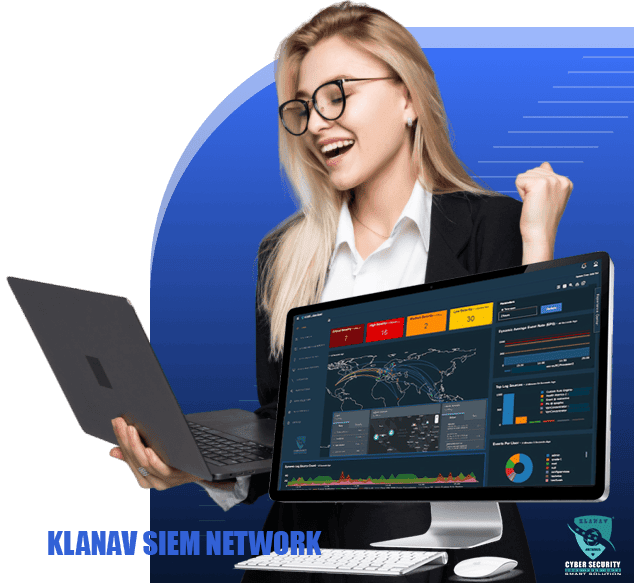
Satisfied Clients
Finished Projects
Skilled Experts
Media Posts


When your password appeared in one of the databases from various internet breaches, follow the instructions in our Leaked password chapter.
A full subscription to Klanav products isn't free. If you decide to purchase Klanav security products, you can use a trial version, which is almost like a full subscription and is free with no set time limit.
If you forgot the PIN to your Klanav application, you must uninstall the application and install it again. However, you will not lose any of your data by uninstalling your Klanav application.
You are trying to verify your subscription using the link in your email address more than 1 hour after receiving the mail. In your KLANAV account, in the Subscriptions section, click All subscriptions > Open Subscription and scroll down to Resend verification email.

Spearphishing is a tactic used to gain initial access in attacks against business systems.